External Connection Rules
If you want to control all the inbound connection requests coming from the outer environment then you should create rules of this type.
To add a rule, click the Network Rules tab of Menu Pane then swith to the External connection rules tab:
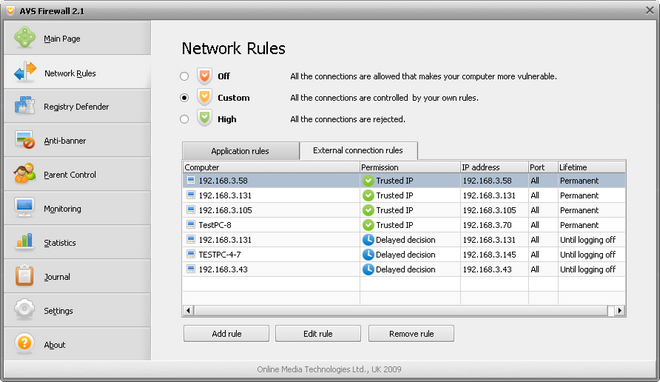
You will see the table of external connection rules that includes the following information fields:
| Computer name |
Shows, if possible, the Netbios or DNS name of a remote computer that initiated an inbound connection. If a rule has been created for a certain port only the field contains the Port rule text; |
| Permission |
Shows the set permission including information what it is applied to:
Trusted IP - the permissive rule for a certain IP-address and all ports associated with it;
Opened port – the permissive rule for a certain port of all IP-addresses;
Trusted IP and port – the permissive rule for a certain IP-address and port associated with it;
Untrusted IP - the prohibitive rule for a certain IP-address and all ports associated with it;
Closed port – the prohibitive rule for a certain port no matter what IP-address is;
Blocked IP and port - the prohibitive rule for a certain IP-address and port associated with it;
Delayed decision - you put off taking a decision on assigning a permission having clicked the Ask me later button in the Alert Window. The temporary rule with the Deny all permission will be created;
|
| IP |
Shows a remote computer IP-address; |
| Port |
Shows a separate port number or the one associated with a certain IP-address; |
| Lifetime |
Shows whether a rule is applied permanently or just until logging off. |
Then press the Add rule button the Create external connection rule window will appear:
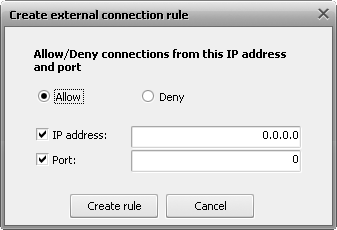
In that window input a remote IP and/or port and assign a permission — either Allow or Deny.
To change or delete a rule, select a row then press the Edit rule or Remove rule button correspondingly.
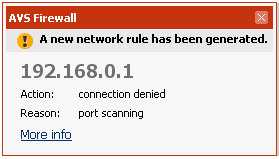
AVS Firewall automatically beats off the port scanning attacks. A certain quantity of inbound requests made in a certain time period and aimed at closed ports is detected as the port scanning attack. The prohibitive rule on an attacking computer IP-address is added in such a case. When the attack occurs, the right bottom corner notification window appears to inform you about that, you can click the More info link to move to the created rule as well:
 Note
Note: if a rule has been added for a network (by means of the
Alert Window) that will be reflected in the table in the following way:

where the rule for the network defines a default permission for all the computers that are included into it unless you add a specified rule for a computer that belongs the network manually:
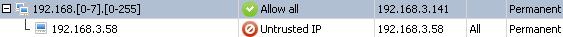
That means permissions specified for computers are stronger than a permission defined for a network they belong to.